As an organization responsible for maintaining patients’ electronic protected health information (ePHI), you are in an industry that is among the most attractive hacking targets for cyber-criminals. The federal privacy laws regulating how you manage this data — particularly HIPAA — are among the strictest and most aggressively enforced of any industry. And as if all of that weren’t concerning enough, your staff is storing and transmitting your ePHI on more mobile devices and in more locations than your IT team can secure, control or even keep track of.
Not a good situation.
So, what can you do to mitigate the substantial risks created as a result of your staff accessing ePHI on devices that might not be properly secured, often in network environments that are also unsecure?
I will offer several suggested solutions below. First, though, let’s define the problems.
Source: HIMSS 2017 Mobile Device Survey
Why Mobile Devices in Healthcare Environments Can be a Security and Regulatory Threat
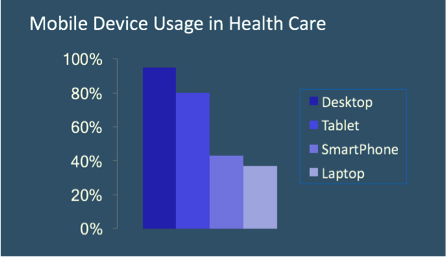
According to a 2017 study on mobile devices in healthcare conducted by the Healthcare Information and Management Systems Society (HIMSS), desktop computers remain the primary device that health professionals use to access patient information for providing and coordinating care. Almost 95% use a desktop.
But nearly 80% of healthcare workers also use tablets, and 42% use smartphones, as part of their daily routines in accessing patient information. The study did not break out this mobile usage into separate categories for company-owned devices and employees’ personal tablets and phones. These numbers likely represent a mixture of both company-issued and personal mobile devices.
(In case you’re curious, the report noted that the reasons tablets seem to be the more popular mobile device are likely that their larger screens allow for more face-to-face interaction with patients, and their larger overall size makes them easier to keep track of within the organization.)
Okay, so healthcare employees are using mobile devices at increasing rates to access their patients’ ePHI. So what?
Well, consider these findings from the Ponemon Institute report, The State of Cybersecurity in Healthcare Organizations in 2016.
– The average healthcare organization experiences a cyberattack almost every month.
– 48% of healthcare providers say they’ve suffered an incident within the last 12 months that led to the loss or exposure of their patients’ ePHI.
– The top two security threats that most worry healthcare IT professionals are: employee-owned mobile devices being used to access ePHI (76%), and any mobile devices accessing ePHI without the proper security installed (72%).
– Finally, 28% of doctors reported storing patient data on personal mobile devices — meaning there could be ePHI data breaches just waiting to happen on more than a quarter of all physicians’ mobile devices.
Also, according to the IBM report Security Trends in the Healthcare Industry, the theft or exposure of patients’ ePHI doesn’t have to be the result of a complex and sophisticated hacking operation. Consider…
– The exposure of hundreds of thousands of patient records can simply be the result of a lost or stolen company laptop without adequate security.
– In one incident in February 2016, a laptop containing ePHI on 400,000 patients was stolen from a healthcare provider’s car.
– Another growing threat to ePHI security is the increasing use of mobile health apps, which are often used on unsecured devices and in unsecured network environments.
Nor can you forget the regulatory risks to your company if your ePHI security practices aren’t up to HIPAA standards. As a report from the HIPAA Journal tells us…
Even under what HIPAA regulators deem a “Category 1” violation, the most minor of all offenses and one that the covered entity was unaware of and could not have realistically avoided, or category 2 in which the company was aware of the problem but it still could not have been avoided, that company could face a maximum fine of up to $50,000, per violation.
– While this level of fine may seem excessive in Category 1 or 2, HIPAA’s federal enforcement arm, the Office of Civil Rights of the Department of Health and Human Services (or OCR), has the discretion to waive the penalty in cases that are not the result of “willful neglect,” which forms the basis for category 3 & 4 violations.
– In addition to action taken by the OCR, a company may also in some cases face fines and penalties from state attorneys-general. Some state healthcare laws have even stricter requirements than HIPAA.
– Finally, for some HIPAA violations the individuals deemed responsible at the covered entities can even face criminal charges. The severity of the charges range from a year in jail where there is reasonable cause or no-knowledge of the violation, up to 10 years behind bars for obtaining ePHI for personal gain or with malicious intent.
8 BYOD Best Practices for Protecting ePHI on Mobile Devices
Okay, enough doom and gloom about the risks of a weak and non-compliant ePHI-security infrastructure! Let me offer you a series of suggested best practices for protecting ePHI in a BYOD mobile/portable environment.
1. First, create clear, concise and comprehensive policies and procedures regarding the handling and protection of ePHI on mobile devices. Document them and disseminate them company-wide. Policies and procedures are of little use if they are not effectively implemented.
2. Create a list of allowed devices and operating systems your staff can use for work and to access ePHI. Devices can include tablets, iPhones, Android or Windows mobile devices, and their associated operating systems. The list may also include wearable devices like Apple or Samsung Watches. (Don’t forget, however, that mobile health apps are a growing source of often unsecured patient data and therefore a juicy target for hackers.)
3. Track and regularly update operating systems, applications and security patches on all of your staffs’ mobile devices that access or store ePHI. Keeping track of multiple devices and operating systems and software updates or patches can be an impossible task without a good mobile device management strategy.
4. Train all healthcare providers and other staff in the secure and compliant use of ePHI on any device in any location. Training personnel to recognize security threats is a critical part of any security strategy, and users need to be especially careful on social media because that is one of the best ways for hackers to gain insider information.
I want to underscore here that if your training does not really engage your employees and provide for continuous learning and reinforcement, it won’t be sufficient to make your staff truly security aware.
5. Make sure your ePHI data is secure “at rest” as well as “in-motion.” That means encryption and good key management, because even the strongest encryption is useless if hackers can get their hands on the keys.
Employ the highest levels of encryption possible for all ePHI transmitted, shared or stored anywhere, whether on the network or in the cloud.
For HIPAA compliance, you must follow the guidelines from the National Institute for Standards and Technology, or “NIST.” NIST strongly recommends Transport Layer Security version 1.2 for protecting data in motion when it is transmitted over a network, and Advanced Encryption Standard (AES) 256-bit encryption for data at rest, while in storage.
6. Demand that employees implement complex password protection for all mobile devices that access ePHI. Users of mobile apps that access or store ePHI should be properly authenticated using a combination of password plus 2-factor.
7. Deploy next-gen security technologies such as Intrusion Detection and Prevention, network segmentation and firewalls. Mobile application traffic should be separated from internal network users and also from guest users, because you don’t know who they are.
8. Implement a Mobile Device Management system, as well as endpoint security management, including tracking and remote wiping of any device that gets lost or stolen.
In fact, Mobile Device Management, or “MDM,” is worthy of its own discussion. So let me dive a little deeper into this topic by offering you six MDM best practices for your organization.

6 MDM Best Practices for Your Organization
The six best practices I’m outlining here are designed both to help tighten your organization’s ePHI and to help bring your BYOD strategy into alignment with HIPAA’s rules and guidelines.
1. Create a dynamic inventory of approved mobile devices, operating systems, and applications. It will not be possible to protect customer data privacy until you have a handle on all the devices that enter and leave your network every day.
Implement a process to maintain the security of those devices. Be especially careful with devices running Android OS because many fake apps out there are vectors for malware, and some devices have in the past even allowed users to manually bypass device security controls.
But even iOS has been shown to be at risk, especially since the Pegasus attack, so vigilance is required for any brand or make of mobile device.
Furthermore, your MDM should have the ability to block access to devices or OS’s that are not approved or not updated with latest versions and security patches. Some people never update anything which creates security holes in the system.
You need to have a designated staff member responsible for lifecycle management and maintenance of all mobile devices on the network to make this happen.
2. Distribute and enforce access control and security policies. Require complex passwords and strong encryption per NIST guidelines for HIPAA compliance.
Again, good key management is critical to application security. If everyone has the same key, that would not be a secure system. Remember, encryption is the best defense against reportable data breaches involving ePHI.
3. Adopt a tracking/deactivation/remote wipe system. You need tools that can keep track of all approved devices in your inventory and a process for what to do when they are lost, stolen or leave the company. Don’t forget that lost or stolen devices are the leading cause of data breaches in healthcare, according statistics from the OCR.
4. Implement a Data Loss Prevention (DLP) program and Cloud Access Security Broker (CASB). This lets you monitor where your data is on any type of endpoint, and control what is going in and out of the network to prevent breaches. A good CASB can also help to block malware and the use of unauthorized cloud services.
5. This should go without saying, but your employees must maintain separation of personal and professional data on BYODs. The best policy is to not allow storage of ePHI on any mobile or portable device; because if you do, they are almost guaranteed to get lost or stolen. A better practice is to use devices to access, view and update patient data without actually downloading and storing it.
6. Don’t forget to balance employee productivity with the need for security. If the requirements are too hard or complex, people either won’t use the application, or they will find a way around the security.
At the end of the day, the most important thing is for your employees to have real-time access to the applications and information they need to do their jobs and provide better patient care.
Don’t Forget HIPAA Compliant Faxing
Finally, as your IT team is upgrading your ePHI-security practices company-wide, keep in mind that if your staff still sends and receives patient information by fax, those communications are regulated by HIPAA as well — and they might well be both unsecure and noncompliant.
Both fax machines and in-house fax servers create vulnerabilities for the data they transmit and store. So your best bet for upgrading your business’s fax infrastructure is to migrate to a fully hosted, cloud fax solution — ideally with a partner that, like us, that’s been helping many of the largest healthcare organizations stay HIPAA compliant and secure for 20 years.
When you outsource your company’s fax processes to the healthcare-faxing experts eFax Corporate, you can bring your faxing in line with HIPAA, even on mobile devices, and you’ll know you are sending and receiving faxes with the most advanced fax security measures. You’ll also always have clear audit trails for record-keeping and audit purposes, and your IT team will have no on-premises hardware or software to purchase, maintain or upgrade. eFax Corporate will even sign a BAA when required for HIPAA compliance. For more information on HIPAA, protection ePHI and Secure Faxing please speak to one of our technical representatives today by calling (888) 532-9265 or requesting a call back.












