Fax / Resources / White Papers / Healthcare IT Cyber Security Update
HEALTHCARE IT CYBER SECURITY UPDATE
Protecting Patient Privacy with Cloud Fax Services
Introduction
Why Healthcare Records Are the Most Attractive Type of Data to Steal
HIPAA Enforcement is Ramping Up Against Covered Entities and Their Business Associates



Real-World Examples of HIPAA Enforcement Actions
Advocate Health Care -$5,550,000
University of Miss. Medical Center -$2,750,000
Oregon State University Health Services -$2,700,000
St. Joseph’s Health System -$2,100,000
Catholic Health Care of Philadelphia -$650,000
Complete P.T. Physical Therapy -$25,000
1. A data breach compromising patients’ health records can result in negative publicity for the covered entity or business associate, which can damage the company’s trust with patients, vendors, stockholders and the general public.
2. HIPAA investigations that result from data breaches or other lapses in compliance can lead to direct fines against the company.
• Failed to perform a risk analysis
• Failed to take corrective action
• Failed to implement access controls
• Failed to get a signed Business Associate Agreement (BAA) with a business associate
• Failed to encrypt a Laptop that was left in an unlocked car overnight.
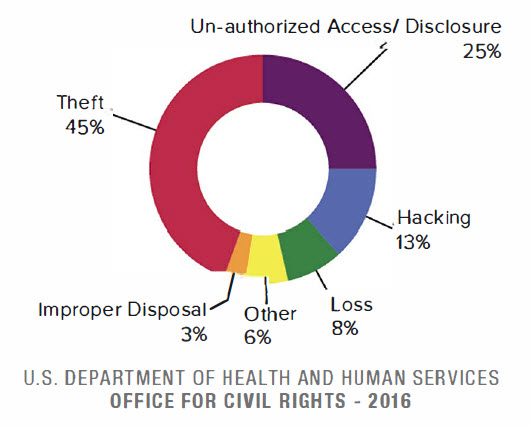
The Causes of Data Breaches - and How to Prevent Them
The Biggest Cybersecurity Concerns for IT Professionals
• Mobile device usage – 58%*
• Data in the public cloud – 57%*
• Cloud infrastructure vulnerabilities – 57%*
• User behavior – 57%*
Compliance in the Cloud - Do Cloud Service Providers Need to Be HIPAA Compliant?
Ransomware: The Fastest Growing Threat to Your Data
1. Does this ransomware attack constitute a “data breach” as defined by HIPAA?
2. Does this attack therefore require a breach notification report to the OCR?
3. What is the probability that your ePHI has been compromised?
Why Compliance Alone Does Not Equal Security
Under the law’s section 45 CFR 164.306, HIPAA demands that covered entities:
• Ensure ePHI confidentiality
• Protect from reasonably anticipated threats
• Use any security measures that comply
Also, under the law’s section 45 CFR 164.312(a)(2)(iv) and 45 CFR 164.312(e)(2)(i), HIPAA refers to a two-factor requirement for ePHI transmission security:
1. ePHI Encryption: A covered entity must
“implement a mechanism to encrypt and decrypt electronic protected health information.”
2. ePHI Integrity: A covered entity must
“implement security measures to ensure that electronically transmitted electronic protected health information is not improperly modified without detection until disposed of.”
What Are the Technical Requirements for ePHI Security?
• ‘Fat-fingering’ fax numbers is a common source of complaints to the OCR.
• If you fax ePHI to an unauthorized recipient, you have just committed a HIPAA violation. It doesn’t matter if it was done by mistake.
• Documents containing PHI may be left unattended on the machines where they are vulnerable to unauthorized viewers.
• If you don’t have a written policy that specifies a set of procedures to secure faxed PHI at both ends, you are not in compliance.
What is Cloud Fax - and Why is it Superior to Traditional Fax?
Why Healthcare Providers Trust eFax Corporate
• NIST Special Pub 800-52 rev1
(Transport Layer Security)
• NIST’s Special Pub 800-111
(Storage Encryption)
• HHS Guidance on HIPAA & Cloud Computing
• Ponemon Institute: Data Security Report
• Cisco 2017 Cybersecurity Report
• Identity Theft Resource Center 2016 Breach Report
The Real Costs of A Data Breach
• 49% of all companies across all industries suffered a data breach in 2016 (Cisco 2017 Cybersecurity Report)
• 1 in 3 patients’ personal data was compromised by cybercrime in 2016 (/DC Research)
• The average cost to the covered entity of each breached healthcare record was $221 (The Ponemon Institute 2016 State of Cybersecurity in Healthcare)
42% lost 20% or more opportunities
38% lost 20% or more customers
39% lost 20% or more revenues
49% had to manage public scrutiny
(Cisco 2017 Cybersecurity Report)
Director HHS Office of Civil Rights
Isn't Fax Always HIPAA Compliant?

• Telco Line Costs None
• Software Costs None
• Hardware Costs None
• Printing Costs None
• Maintenance Costs None
• Power/Rackspace Costs None
- Our solutions are trusted by many of the world’s leading businesses in heavily regulated industries.
- We prov ide service to near ly half of the Fortune 500 companies worldwide.
- eFax Corporate is certified for HIPAA compliance. Will sign HIPAA Business Associate Agreement.
- Faxes in transit and at rest are secured with the strongest NIST approved encryption standards – TLS 1.2 and 256 -bit AES.
- eFax Corporate is already compliant with PCI-DSS v.3.2 encryption requirements for 2018.
- Consensus® has invested millions of dollars to build a secure, compliant and redundant global cloud fax network.
- eFax Corporate operates on a geographically diverse global network comprised of redundant data centers and Tier Ill/IV rated colocations providing 99.9% server uptime.
- SLA for service availability and rapid Fax delivery. 24/7/ 365 customer support.